
Traefik with docker-compose
What is Traefik and how does it work?
Traefik is a tool that can be used to manage and route traffic and requests in a modern, cloud-native environment. Traefik is one of the most popular tools for managing and routing traffic in today’s environments, and it’s easy to see why. Many organizations that use microservices and containers rely on Traefik to manage their traffic.
It’s designed to work well with containers and orchestration systems, and it supports a wide range of service discovery providers, such as docker, consul, and kubernetes. This means that Traefik automatically finds new services and routes traffic to them, without having to manually configure them.
The Traefik platform includes core reverse proxy as well as load balancing capabilities. It also supports SSL termination and health checks, as well as circuit breakers and it also has a web dashboard that monitors and manages your infrastructure.
Traefik’s core features are highly configurable, but you can also add custom functionality with its powerful plugin system.
Traefik acts as a reverse proxy server that sits between a client request and the backend service that processes that request. It checks incoming requests and uses a set of routing rules to determine how to route those requests to the backend service.
When a request arrives at Traefik, it first inspects it and extracts information from the request, such as the request URL, the request headers, etc. The information is then used to decide which backend service should handle the request.
Traefik’s routing rules are based on various parameters, including the hostname of the incoming request, the path to the request, and the header values.
Once Traefik decides which backend service to forward the request to, it forwards that request to the backend service and forwards the response to your client.
One of the main advantages of using Traefik over other services is that it automatically detects and routes traffic to the backend services without any manual configuration. For example, if a new service is added or removed from Traefik, the traffic to the backend service will automatically be routed to that service.
Another advantage is that Traefik supports a variety of service discovery providers, such as Docker
The overall conclusion is that Traefik offers a powerful and adaptable tool that offers a broad range of features for traffic and request management in today’s cloud-native infrastructures. Automatically discovering and routing traffic to the backend services makes Traefik an attractive choice for enterprises using microservices and containers.
Getting Started
Requirements
You need to have docker installed on your computer. If you don't have it jet follow the instructions from the docker docs.
Create a Docker network
Traefik needs a external network to communicate to your other Docker containers. To do this, open a terminal and execute the following command:
docker network create traefik_netCreate a configuration file for Traefik
The first thing you need to do is to create a Traefik configuration file. This file will tell Traefik how to route traffic. To do this, create a new traefik.yml file and add the following:
## traefik.yml
#
# STATIC CONFIGURATION
global:
checkNewVersion: true
sendAnonymousUsage: false
log:
level: "INFO"
accessLog:
filePath: "/logs/access.log"
bufferingSize: 100 # Configuring a buffer of 100 lines
filters:
statusCodes: "204-299,400"
api:
insecure: true
dashboard: true
entryPoints:
web:
address: ":80"
http:
redirections:
entryPoint:
to: websecure
websecure:
address: ":443"
http:
middlewares:
- secureHeaders@file
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
file:
watch: true
directory: “/etc/traefik/dynamic_conf”In this configuration file we created two access points to listen.
1) web ( Port 80 HTTP ) with a redirect to the entry point websecure
2) websecure ( Port 443 HTTPS ) where we access a middleware with secureHeaders
If you don't want to use SSL do not add the redirect so remove the http: part from the web entry point.
Create your .crt and .key file ( optional )
For testing or your local development area you can create self signed certificates with:
openssl req -x509 \
-sha256 -days 356 \
-nodes \
-newkey rsa:2048 \
-keyout YOUR_KEY_FILE.key -out YOUR_CERT_FILE.crtCreate your TLS configuration file
To use your traefik over ssl you need to add a cert to resolve and add this to tls.yml.
## tls.yml
http:
middlewares:
secureHeaders:
headers:
sslRedirect: true
forceSTSHeader: true
stsIncludeSubdomains: true
stsPreload: true
stsSeconds: 31536000
tls:
stores:
default:
defaultCertificate:
certFile: /tls/YOUR_CERT_FILE.crt
keyFile: /tls/YOUR_KEY_FILE.key
certificates:
- certFile: /tls/YOUR_CERT_FILE.crt
keyFile: /tls/YOUR_KEY_FILE.keyCreate your docker-compose.yml
If you don't use SSL use as entrypoint web not websecure.
## docker-compose.yml
version: "3.8"
networks:
default:
name: "traefik_net"
external: true
services:
traefik:
image: "traefik:latest"
container_name: "demo_traefik"
hostname: "demo"
network_mode: "host"
restart: "unless-stopped"
volumes:
- "./traefik.yml:/traefik.yml:ro"
- "/var/run/docker.sock:/var/run/docker.sock:ro"
- "./tls.yml:/etc/traefik/dynamic_conf/conf.yml:ro"
- "./tls-data:/tls:ro"
labels:
- "traefik.enable=true"
- "traefik.docker.network=traefik_net"
# HTTPS Routers
- "traefik.http.routers.demo_traefik.rule=Host(`traefik.localhost`)"
- "traefik.http.services.demo_traefik.loadbalancer.server.port=8080"
- "traefik.http.routers.demo_traefik.tls=true"
- "traefik.http.routers.demo_traefik.entrypoints=websecure"Start your docker-compse.yml
Now you can start your service with:
docker compose up -dnow you can access the traefik dashbord at https://trafik.localhost or http://traefik.localhost.
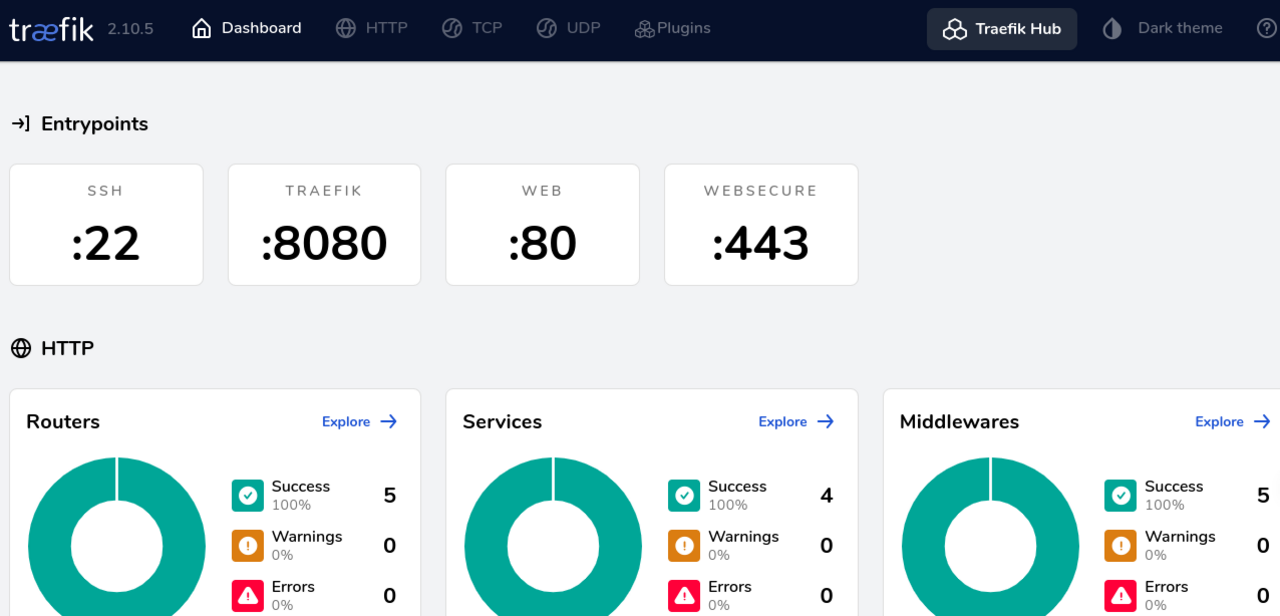
you can find the example on my git server.






